Exploring social network analysis for understanding terrorism 🦹
Table of contents
What is social network analysis and how can it be applied to help us understand the structure and dynamics of terrorist networks? We’ll demystify the basics of centrality, community and show you how it can reveal the inner workings of terrorist groups.
You can access an interactive Streamlit dashboard here: Link
Terrorist and random network analysis
This project examines terrorist social networks using data available from data information sources in Valdis Krebs’ article. Specifically, we examine the network surrounding the tragic events of September 11, 2001. The September 11, 2001 attacks were four Islamist suicide attacks carried out on the same day in the United States. With the dataset, we are able to map a part of the network centered around the 19 deceased hijackers. This network gives us an insight into the terrorist organization.
1. Description
The September 11, 2001 attacks were four Islamist suicide attacks carried out on the same day in the :flag_us:United States, causing the deaths of 2,977 people. They took place in Manhattan, New York, Arlington in Virginia, and Shanksville in Pennsylvania. Nineteen terrorists hijacked four commercial airplanes. Two planes, 🛩️ AA 11 and 🛩️ UA 175, controlled respectively by Mohamed Atta and Marwan al-Shehhi, were flown into the Twin Towers of the World Trade Center (WTC) in Manhattan (New York), while a third plane was flown into the Pentagon, the headquarters of the Department of Defense, in Washington, D.C., killing all the people on board and many others working in these buildings. The third plane, 🛩️ AA 77, controlled by Hani Hanjour, was also flown into the Pentagon. The fourth plane, 🛩️ UA 93, controlled by Ziad Jarrah, crashed in a field in Shanksville, Pennsylvania.
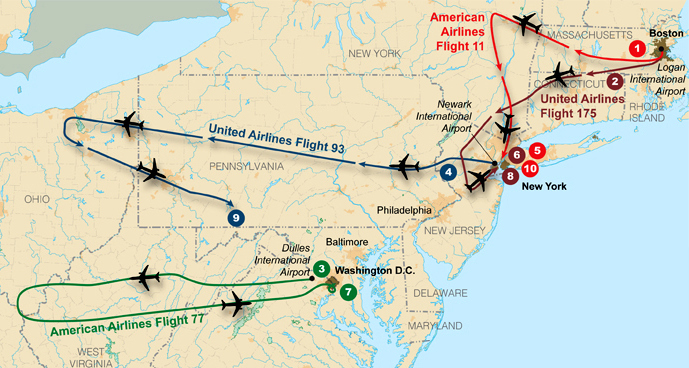
We will discover the formation of terrorist social networks. The “Hamburg cell” was a group of radical Islamists based in Hamburg, Germany on November 1, 1998, which included students from different Arab countries who eventually became key agents in the September 11 attacks. They are the important members: Marwan al-Shehhi , Ziad Jarrah and Mohamed Atta, who led the four hijacking teams, . They arrived in the United States in mid-2000 to conduct flight training. Other members included Said Bahaji, Zakariya Essabar, Mounir el-Motassadeq and Abdelghani Mzoudi. And Ramzi bin al-Shibh, who conspired with the other three members but was unable to obtain a 🛂 visa to enter the United States. It was later replaced with Hani Hanjour. But the first hijackers to arrive in the United States were Khalid al-Mihdhar and Nawaf al-Hazmi in January 2000.
2. Characteristics
With the data from the table below, we can see that our social network has 62 nodes, including hijackers and co-conspirators. Thus, the density is 0.0804, which is quite low, indicating that the graph is sparse and there are relatively few links between nodes. The number of connected components in a graph is equal to 1, meaning that all nodes in the graph are connected to each other by a path. There are no subsets of nodes that are disconnected from each other and cannot be reached from one another. In this case, the graph is a connected graph. The average number of links that a node has in the graph, or the average degree, is equal to 4.9. The farthest nodes from each other are separated by 5 links. The average distance between all pairs of nodes is 2.94 links. A clustering coefficient of 0.49 would indicate that the nodes in a network are moderately well-clustered.
| Number of nodes | Number of edges | Directed graph | Number of Components | Average degre | Density | Diameter of Network | Average Shortest Path | Clustering |
|---|---|---|---|---|---|---|---|---|
| 62 | 152 | False | 1 | 4.903 | 0.08 | 5 | 2.946 | 0.486 |
Conclusion: The 19 hijackers did not act alone. They had 43 other accomplices who did not board the plane. These co-conspirators are money generators and also provide the skills and knowledge needed. Networks expose the hijackers and their network neighborhoods - their direct and indirect associates. There are a total of 152 links between 62 members. It is surprising that there are 10 co-conspirators who have less than 20 direct links with the hijackers (excluding the “Hamburg Cell”). The other co-conspirators have direct and indirect links with the “Hamburg Cell”. This indicates that my network seems to be divided into two halves separated by the “Hamburg Cell”. The distance between hijackers on the same team is also very low. Many pairs of team members were beyond each other’s observability horizon - many on the same flight were more than two steps away from each other. This is like a strategy to keep team members apart from each other and other teams, minimizing damage to the network if a cell member is captured or otherwise compromised.
3. Centrality
Degree centrality
Degree centrality is the most straightforward centrality measure we will explore. It quantifies the importance of a node based on the number of direct connections it has within the network. In social networks, degree centrality is a measure of popularity and can be a good way to guess who is in charge. Degree centrality is a fairly rudimentary example, but the following sectionspresent more complex solutions commonly used in network science. The first three Mohamed Atta , Marwan al-Shehhi , and Hani Hanjour are pilots, while the 4th pilot Ziad Jarrah is ranked 7th because he has fewer neighbors compared to the other pilots.Mohamed Atta ’s degree centrality is 0.36, which is much higher than the individuals below because he has the most links.
| Index | Degree centrality | Person |
|---|---|---|
| 11 | 0.360656 | Mohamed Atta |
| 31 | 0.295082 | Marwan al-Shehhi |
| 43 | 0.213115 | Hani Hanjour |
| 44 | 0.180328 | Nawaf al-Hazmi |
| 1 | 0.180328 | Essid Sami Ben Khemais |
| 24 | 0.163934 | Ramzi bin al-Shibh |
| 30 | 0.147541 | Ziad Jarrah |
| 40 | 0.147541 | Abdul Aziz Al Omari |
Closeness centrality
The goal of closeness centrality is to study whether the node is close to other node and can interact with them quickly. The idea is to look at the distance between the nodes. The closeness centrality increases if its distance to other nodes is low. The first three Mohamed Atta , Marwan al-Shehhi , and Hani Hanjour are pilots, while the 4th pilot Ziad Jarrah does not appear becausethe distance to other nodes is high. Mohamed Atta ’s distance to other nodes is lower because his closeness centrality is equal to 0.58, which is the highest.
| Index | Closeness centrality | Person |
|---|---|---|
| 11 | 0.580952 | Mohamed Atta |
| 31 | 0.462121 | Marwan al-Shehhi |
| 43 | 0.442029 | Hani Hanjour |
| 44 | 0.438849 | Nawaf al-Hazmi |
| 15 | 0.432624 | Zacarias Moussaoui |
| 24 | 0.432624 | Ramzi bin al-Shibh |
| 1 | 0.429577 | Essid Sami Ben Khemais |
| 40 | 0.420690 | Abdul Aziz Al Omari |
Betweenness centrality
Betweenness centrality is based on the assumption that the higher the number of shortest paths passing through a node, the more it acts as a broker (or a bridge). To calculate betweenness centrality, the shortest paths between each pair of nodes are found. The betweenness centrality value for a node or an edge is simply the numberof these paths that pass through it. The goal of betweenness centrality is to measure how important a node is in connecting two other nodes in the graph or how a node serves as an intermediary. It alsomeasures the usefulness of the node in communication and information transfer within the graph. The statistics of Mohamed Atta are much higher than the others becausehe plays an important intermediary role in the network. Meanwhile, Essid Sami Ben Khemais and Zacarias Moussaoui are the ones who linkMohamed Atta to other co-conspirators. So, they have just a slightly higher measure than the other pilots. Similar to the previous measure, the 4th pilot Ziad Jarrah does not appear on the list.
| Index | Betweenness centrality | Person |
|---|---|---|
| 11 | 1074.215573 | Mohamed Atta |
| 1 | 459.973443 | Essid Sami Ben Khemais |
| 15 | 415.416667 | Zacarias Moussaoui |
| 44 | 281.939683 | Nawaf al-Hazmi |
| 43 | 230.985462 | Hani Hanjour |
| 17 | 221.583333 | Djamal Beghal |
| 31 | 162.933836 | Marwan al-Shehhi |
| 39 | 92.178125 | Satam Suqami |
Eigenvector centrality
Eigenvector centrality is based on the analysis of the eigenvectors of the adjacency matrix of a graph. This measure is oftenused to identify community leaders in social networks. The interesting thing is that the 4th person Ziad Jarrah is also the 4th pilot because he is connected to theother 3 important pilots. A higher eigenvector score for Mohamed Atta means that he is connected to many nodes that themselves have high scores. We can also see that the other nodes are all very close toeach other, they are not separated like in the previous three algorithms.
| Index | Eigenvector centrality | Person |
|---|---|---|
| 11 | 0.412506 | Mohamed Atta |
| 31 | 0.399862 | Marwan al-Shehhi |
| 43 | 0.246944 | Hani Hanjour |
| 30 | 0.241743 | Ziad Jarrah |
| 40 | 0.238062 | Abdul Aziz Al Omari |
| 24 | 0.223737 | Ramzi bin al-Shibh |
| 29 | 0.215109 | Said Bahaji |
| 35 | 0.202387 | Fayez Ahmed |
Comparison
| Index | Degree centrality | Closeness centrality | Betweenness centrality | Eigenvector centrality |
|---|---|---|---|---|
| 11 | Mohamed Atta | Mohamed Atta | Mohamed Atta | Mohamed Atta |
| 31 | Marwan al-Shehhi | Marwan al-Shehhi | Marwan al-Shehhi | Marwanal-Shehhi |
| 43 | Hani Hanjour | Hani Hanjour | Hani Hanjour | Han Hanjour |
| 44 | Nawaf al-Hazmi | Nawaf al-Hazmi | Nawaf al-Hazmi | -1 |
| 1 | Essid Sami Ben Khemais | Essid Sami Ben Khemais | Essid Sami Ben Khemais | -1 |
| 24 | Ramzi bin al-Shibh | Ramzi bin al-Shibh | -1 | Ramzi bin al-Shibh |
| 30 | -1 | Ziad Jarrah | -1 | Ziad Jarrah |
| 40 | Abdul Aziz Al Omari | Abdul Aziz Al Omari | -1 | Abdul AzizAl Omari |
| 15 | -1 | Zacarias Moussaoui | Zacarias Moussaoui | -1 |
| 17 | -1 | -1 | Djamal Beghal | -1 |
| 39 | -1 | -1 | Satam Suqami | -1 |
| 29 | -1 | -1 | -1 | Said Bahaji |
| 35 | -1 | -1 | -1 | Fayez Ahmed |
Conclusion: We see the 3 first pilots appear 4 times in the table above, which confirms that these 3 pilots played an important role. Unlike the other pilots, Nawaf al-Hazmi was considered the second-in-command of the attack. He also initially underwent pilot training but did not complete it. As we know, there were only 19 hijackers. Ramzi bin al-Shibh was selected as the “20th hijacker” to be one of the pilots, but was unable to enter the US. Both of these individuals have links to Mohamed Atta , but Nawaf al-Hazmi does not have the same links to other pilots like Ramzi bin al-Shibh who have high eigenvector centrality scores. Therefore, Nawaf al-Hazmi does not appear on the eigenvector centrality list.
4. Community
The main goal of community detection is to partition the nodes of a graph into a finite number of groups and to find homogeneous groups of nodes, meaning individuals with similar behavior. By community, we mean a subset of nodes that are strongly connected, i.e., there are a significant number of connections between them, more than what these nodes have with other members of the network. We can quickly find a link between the hijackers and also discover some of the associates of the hijackers. Being associated with a terrorist does not prove guilt, but it can help the investigation process.
The properties of the Clauset-Newman-Moore and Girvan-Newman algorithms are similar, but the Girvan-Newman algorithm focuses more on analyzing links in the network to identify communities, while the Clauset-Newman-Moore algorithm focuses on analyzing nodes. The Louvain algorithm is generally considered to be faster and more efficient than the Clauset-Newman-Moore and Girvan-Newman algorithms because it does not require specifying a number of communities in advance and is able to find communities of varying sizes. To construct a clandestine network, one must identify task and trust links between conspirators. These networks often do not behave like normal social networks. Conspirators do not form many links outside of their immediate cluster and often minimize activation of existing links within the network. Tight links between previous contacts, often formed years ago in school and training camps, keep the cells linked. Yet, unlike normal social networks, these strong links largely remain dormant and thus hidden to outsiders.
References and useful links
Uncloaking Terrorist Networks by Valdis E.Krebs: https://journals.uic.edu/ojs/index.php/fm/article/view/941/863
Network catlogue, repository and centrifuge data Netzschleuder: https://networks.skewed.de/net/terrorists_911
“Mapping networks of terrorist cells." Connections 24, 43-52 (2002)
Network Analysis & Visualisation: Game of Thrones Character Network Link